You might think you understand the concept of BadUSB attacks and know how to protect it, because all you’ve noticed is opening a terminal window. As it turns out, there’s even more attack surface to cover, as [piraija] tells us in his USB-HID-and-run post. If your formula doesn’t perform scrupulous filtering of HID devices, you may be vulnerable to some sort of BadUSB attack that you haven’t noticed yet, rumor has it that some ATMs have been hacked; simply shutting down the same old BadUSB routes may not be enough. I don’t.
The culprit is the Consumer Control specification, a hard-to-understand component of the popular HID that defines multimedia buttons, particularly the “start browser” and “open calculator” types of buttons seen on some keyboards, whose operating formulas, interestingly, have a tendency to support. If the underlying operating formula you use for kiosk purposes is rarely very much configured to bypass those buttons, they’ll offer any attacker unforeseen tactics to bypass your kiosk environment, and it works strangely well.
[Piraija] tells us that this attack gives us a lot of opportunities, as he tested it on various devices in the wild. For your own testing, the article has an Arduino code pattern that you can download to any USB-enabled microcontroller. and for the better-equipped hackers, we even get a Flipper Zero app that they can use instead. While we’ve noticed some doubts about whether USB devices can be a suitable attack vector, modern operating systems are more complex and gigantic than they seem. , with almost no explanation as to why; for example, if you’re using Windows 10 or 11, press Ctrl Shift Alt Win L and you’re done. And, of course, you can create a hostile USB implant small enough to have USB compatibility. C charger or docking station.
USB image: Inductive charging, public domain.
Once upon a time, when telephones were still working and modems were proud to compose a song out of their people’s songs, I sent for a set of Slackware CDs and embarked on a remarkable journey. Back then, running Linux (especially on the desktop) wasn’t a task to be taken lightly. The kernel itself was still evolving considerably: instead of modifying a hard-to-understand subsystem or adding a niche device you don’t even own, the new editions unlocked critical features and entire categories of devices. I still haven’t forgotten to decide whether I was looking to play it safe and stick with my existing kernel, or try my luck by compiling the most recent edition to notice this new “USB mass storage” that everyone was talking about on the forums. . .
But modern desktop Linux has reached a point of majority and is now a viable option for a large number of PC users. In fact, if you add Android and Chrome OS to the mix, millions and millions of people use Linux daily without even knowing it. it. Nowadays, the only way to revel in that sense of adventure and wonder that once arrived here pre-loaded with a Linux box is to go through and get it.
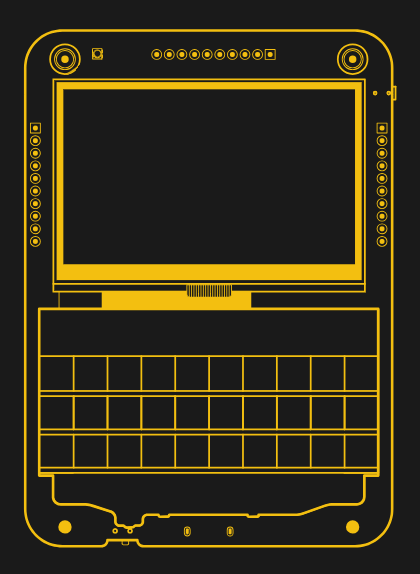
This is exactly what it feels like to use SQFMI Beepy. The handheld device, once known as the Beepberry before its creators won an all-too-predictable formal complaint, is unabashedly designed for Linux nerds. Over the past few weeks, while playing with this first-run hardware, I compiled kernel drivers, wrote traditional scripts, and tried (but failed) to install new software on it. If you like to hack Linux, this is a real treat.
Chances are, you already know whether Beepy is for you or not, but if you’re still unsure, this in-depth review of the hardware and current state of the overall task can help you make a decision before SQFMI officially launches. . starts receiving new orders for the $79 device.
Continue “Review: Beepy, A Palm-Sized Linux Hacking Playground” →
If you’ve ever searched for open-source e-readers, you’ve no doubt noticed [Joey Castillo’s] Open Book Reader, but you may not have noticed the abridged edition you’re building around a Raspberry Pi Pico yet.
The Open Book project combines a 4. 2-inch e-ink display with microprocessors we all know and love, creating a hacker-friendly e-reading platform. Two years ago, this project won first place in our Adafruit Feather contest: Feather’s footprint makes the Open Book compatible with a wide diversity of MCUs, giving hackers a choice of which processor their hackable e-reader would run on. Now it’s time to reboot the RP2040.
This task is designed so that you can put it together yourself after purchasing portions and PCBs. To help you with the process, the PCB itself looks like a page out of a book: in screen printing, there are explanations about the function of the component. , as well as data that would come in handy when hacking, relaying the history of the hardware to the hacker who is about to embark on the meeting with a soldering iron in hand. There’s also undeniable, but completely useful, software to stream along with this hardware and as completely open-source gadgets disappear and missing features can be added.
Joey recorded a 30-minute video of the Pi Pico edition for us, assembling and testing the newly ordered boards, and then showing how the software boots up and works properly. The Pi Pico-based review has been greatly simplified, with a number of self-assembly aspects improved compared to previous editions: the total procedure takes less than an hour and is also performed with a fairly basic soldering iron.
If you’re looking for updates on this review as progress progresses, following [Joey] on Twitter is your most productive bet. He’s no stranger to making the devices around us freer and then sharing the secret sauce with all of us!During Remoticon in 2021, it showed off a replacement motherboard for the Casio F-91W wristwatch and told us all about the opposite engineering that its controllerless LCD segment shows – it’s worth a listen to for any hacker ever looking to bend those LCD screens.
Continue “Abbreviated Open Book: The OSHW E-Reader Now Simplified and Powered Through Pico” →
When reviewing a project, it’s easy to get tired of an uncooked parts list. When the main component is a ESP8266, you can just say, “Oh, some other 8266 project. Yawn!” But we’re sure that when you take a look at [Will Fox’s] Foxie CardClock, it’s going to catch your eye.
As if all those beautiful LEDs weren’t enough, the rest of the device’s specs are pretty impressive. The fundamental parts may be common, but what separates these projects is the software. With Over The Air upgrades supported through ArduinoOTA, upgrades are a breeze. A soft sensor helps keep all LEDs at a moderate level, and a once-per-minute synchronization via NTP helps keep the time accurate. Even in the event of a power failure, a supercapacitor can keep accurate time. for up to two days thanks to the built-in PSTN module. There are even provisions to set the time using the buttons on the front panel if you need to keep the device offline.
The entire task is open source, with the curtains released under the CERN Open Hardware License edition 2 and the firmware source code distributed under GPLv3. Users are encouraged to hack and edit the design, and all the data you want to create is yours. can be obtained from the task’s GitHub repository. [Will] also offers a pre-assembled edition of the watch for just $45 USD, but unfortunately, it seems to be out of stock at the time of writing.
If credit card-sized gimmicks are your selected domain of interest, enjoy this crystal radio made with a genuine credit card. Thanks to [Abe] for presenting the advice!
The principles of open source hardware are beginning to make wonderful strides in the fields of clinical studies. [Walker Arce] talks about his paper co-authored with [Jeffrey R. Stevens], about a dog treat dispenser designed with clinical studies in the brain: indispensable for behavioral studies purposes and reproducible seamlessly so that our science can also be replicated. The use of Raspberry Pi, NEMA stepper motors, and many parts published in 3D make this build reasonable ($<200 USD) and easy to repeat for any experiment with dogs or other treat-loving animals.
Even if you’re not a scientist, you can still build one to educate your own puppy – this style is that undeniable and undeniable to replicate!Most of the portions are amateur grade, and there’s a good chance you’ll be able to locate the maximum of the mandatory portions in your workshop. Wondering how this dispenser works and, more importantly, if dogs are satisfied with it?Watch a short demo video after the break.
Although these dispensers are commercially available, having a new type of dispenser designed and verified is more valuable than expected: the authors report that, in their experience, commercially available dispensers have an error rate of 20 to 30%, while theirs may boast only 4%, and have verification effects to back it up. We still can’t be satisfied that the most productive interpreter is available to one and both of them. The GitHub repository has one and everything you could ever need: from STL and PCB files to a Raspberry Pi SD card symbol and a 14-page PDF meeting and setup guide.
Open curtains and science go hand in hand, even if the appointments are still unfolding. The La-Tecnologia network has already combined to talk about open science hardware, and from time to time, open-source clinical apparatus graces our pages, just like this recent one. Collection of biodetection tricks from repurposed client devices.
Continue “The Open Material Dog Treat Dispenser Is a Stepping Stone to Behavioral Research” →
Often, we want to force one of our 5V strength-hungry projects on the fly. [Burgduino] followed suit and, dissatisfied with the answers available, designed his own 5V inverter. A reasonable force bench design is needed and increases it through a few important portions for your UPS goals.
You might be tempted to opt for a power bank when faced with such a problem, but most of them have a fatal flaw, and you can’t easily distinguish a faulty battery from a working one before you buy it. This flaw lies in the lack of load sharing: the ability to continue to force out when a charger is inserted. Most store-bought power banks simply shut down the outlet, which prevents a task from running 24/7 without shutting it down, and can have adverse consequences when dealing with a device like a Raspberry Pi.
Naturally, [Burgduino] did not agree with this. Its UPS is based on the TP5400, a combined LiIon charging and ignition chip, which is widely used in undisputed powerbanks, but is not capable of charging percentage. For this, another LM66100 chip is used, an “ideal diode” driver. used. You might scoff at the fact that it’s a Texas Instruments part, but it happens to be widely available and a bit more expensive than the TP5400 itself!The design is open hardware, with PCB files available in EasyEDA and the invoice for the fabrics is obviously designed to make it easier to order from LCSC.
Hackers can find it difficult to keep our portable Pi projects running, employ supercapacitors, and modify poorly designed Chinese boards. However, once we’ve figured out a toolset that suits our needs, battery-powered projects tend to open up new frontiers. You can even go beyond your Pi and upgrade your router with a UPS add-on!Of course, navigation is rarely very smooth and rarely can easy-to-carry devices surprise you with their design quirks.
For the past few months, we’ve been keeping an eye on WiFiWart, an ambitious task to expand a Linux single-board computer (SBC) small enough to have compatibility with a USB wall charger. The expander [Walker] says the purpose is to create a “Mailbox” that can be easily hidden for penetration testing, giving security researchers a valuable foothold within a target network from which to explore or launch attacks. Of course, we don’t want to tell The-Technology readers that there are many other things you can do with such a small open-hardware Linux SBC.
Today, we’re pleased to announce that [Walker] has the first edition of the map on Linux, although, unsurprisingly given a task of such complexity, there were some bumps in the road. From the lack of resiliency that caused a U-Boot error to the intricacies of compiling the kernel for an embedded board, the most recent blog post he wrote about his progress provides a desirable insight into the small mistakes of creating an SBC from scratch.
Once the board booted up on Linux, [Walker] started checking other aspects of the system. A memory check showed that the delicate DDR3 RAM worked as expected and was able to load the kernel modules for dual interfaces RTL8188 and connect to a network. Although WiFi modules have been hanging from the board’s full-size USB ports lately, they will eventually be incorporated into the PCB.
This prototype board also provides [Walker] with a concept of the ultimate hardware force input. Even with a full tilt, this larger plate does not exceed five00 mA at five VDC; so if you design the power source with a maximum output of 1 A, you have a large margin of safety. As discussed in the previous post, there are plans lately to place the power supply on its own board, which will allow for more effective use. of the internal volume of the charger.
With software and hardware now largely locked down, [Walker] says his focus will be on making everything small enough to have compatibility in the ultimate form factor. In fact, this will be the most challenging facet of the project, but with a developing network of hackers and engineers bringing their expertise to the cause, we are confident that WiFiWart will soon be a reality.