ESET Cybersecurity Corporation released a report detailing a new strain of Windows malware that the company named KryptoCibule.
ESET claims that the malware has been distributed at least since December 2018, but has only now made the impression on your radar.
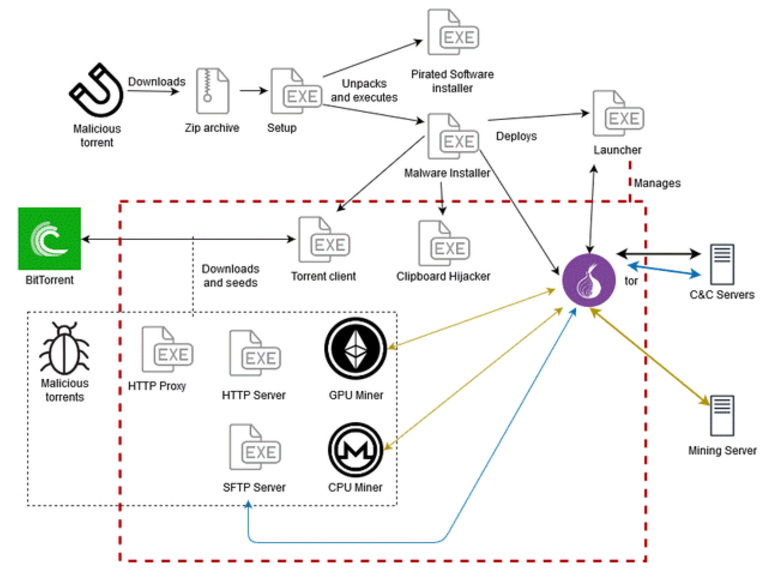
According to the company, KryptoCibule is intended for cryptocurrency users, the 3 main features of malware are (1) installing a cryptocurrency miner on victims’ systems, (2) using borrowed files similar to the cryptocurrency wallet and (3) updating wallet addresses on the operating system’s paperweight to divert payments into cryptocurrencies.
These features are the result of extensive progression through the malware’s creators, who have gradually added new elements to KryptoCibule’s code since its first release in 2018.
According to ESET, malware has slowly evolved into a complex multi-component threat, well above what is seen in the maximum of other malware strains.
Currently, the malware broadcasts torrent files for pirated software. ESET says that users who download those torrents will install the hacked software they wanted, but they will also run the malware installation program.
This installer implements a restart patience mechanism that relies on scheduled tasks, then installs the KryptoCibule malware core (the launcher), the operating formula clipboard hacking module and Tor and torrent clients.
ESET says kryptoCibule uses the Tor consumer to talk securely with their command and servers (C
Overall, KryptoCibule is bad news for cryptocurrency users, as it is obviously a variety designed by other people familiar with fashion malware operations.
However, there is also good news, at least for now.ESET says this is a rather complex threat, the distribution of KryptoCibule appears to have been limited to only two countries, namely the Czech Republic and Slovakia.
ESET researchers claim that almost all malicious torrents that distribute KryptoCibule-related hacked software were only available on uloz.to, a popular file-sharing site in both countries.
This limited distribution turns out to have been planned from the outset, because KryptoCibule is also a feature that verifies the presence of antivirus software on the victim’s computer, and this module only checks the presence of ESET, Avast and AVG, the 3 funded antivirus corporations.either in the Czech Republic and Slovakia, and probably on the computers of the maximum target users.
However, the fact that this strain of malware is distributed lately only in a small domain of the world does not explain why it will continue to be so in the future.
Users remain vigilant, and the easiest way to avoid a risk like KryptoCibule is not to install hacked software Various reports over the past decade have warned users that the maximum torrent files for pirated software are regularly connected with malware and do not value the risk.
AusCERT says the alleged Hacking of the DoE Came Here from a Third Party
CISA and the FBI say they have noticed cyberattacks this year on voter registration databases.
Russian Facebook and Twitter propaganda accounts following FBI advice
Norwegian Parliament Reveals CyberAttack on Internal Messaging System
By registering, you agree to the terms of use and knowledge practices defined in the privacy policy.
You’ll get a loose subscription to ZDNet’s Tech Update Today and ZDNet Announcement newsletters.You may opt out of receiving these newsletters at any time.
You agree to get CBS circle updates, alerts, and promotions from business family members by adding the ZDNet Technology Update today and the ZDNet Announcement.You can opt out at any time.