Malicious actors are exploiting a new attack strategy that leverages specially crafted saved Management Console (MSC) save files to achieve full execution of Microsoft Management Console (MMC) code and evade security defenses.
Elastic Security Labs named the technique GrimResource after identifying an artifact (“sccm-updater. msc”) that was uploaded to the VirusTotal malware scanning platform on June 6, 2024.
“When a malicious console record is imported, a vulnerability in one of the MMC libraries can lead to the execution of malicious code, adding malware,” the company said in a message shared with The Hacker News.
“Attackers can combine this strategy with DotNetToJScript for arbitrary code execution, which can lead to unauthorized access, recipe hijacking, and much more. “
The use of log types as a vector for malware distribution is seen as an attempt by adversaries to overcome the security barriers erected by Microsoft in recent years, adding the disabling of default macros in Office logs downloaded from the Internet.
Last month, South Korean cybersecurity firm Genians detailed the use of a malicious MSC registry through the North Korean-linked hacking organization Kimsuky for malware.
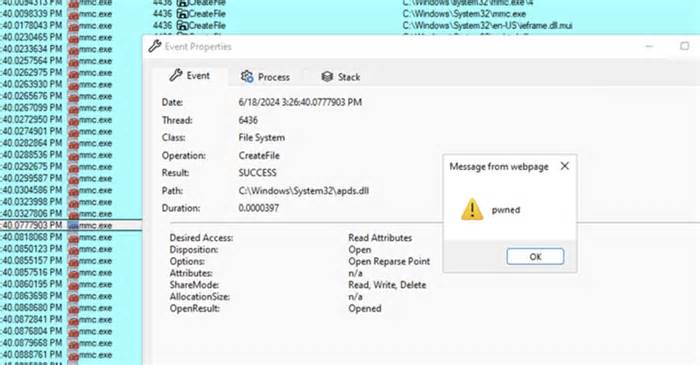
GrimResource, on the other hand, exploits a cross-site scripting (XSS) flaw in the apds. dll library to execute arbitrary JavaScript code in the context of MMC. The XSS flaw was first reported to Microsoft and Adobe in late 2018. , has not yet been patched.
This is completed by adding a reference to the vulnerable APDS resource in the StringTable segment of a malicious MSC file that, when MMC is opened, triggers JavaScript code execution.
Not only does the strategy bypass ActiveX warnings, but it can also be combined with DotNetToJScript to achieve arbitrary code execution. The analyzed pattern uses this technique to launch an ArrayNET loader component called the PASTALOADER that paves the way for Cobalt Strike.
“After Microsoft disabled Office macros by default for Internet documents, infection vectors such as JavaScript, MSI files, LNK and ISO objects gained popularity,” said security researchers Joe Desimone and Samir Bousseaden.
“However, these other strategies are analyzed by defenders and have a high probability of being detected. The attackers have developed a new strategy to execute arbitrary code on counterfeit MSC files in the Microsoft Management Console. “
Continuous attack discovery and penetration testing
Continuously discover, prioritize, and mitigate exposures with evidence-based ASM, Pentesting, and Red Teaming.
Facing identity threats? Learn how ITDR can protect you against ransomware and lateral movement attacks.
From knowledge breaches to identity theft, compromised credentials can cost you everything. Learn how to prevent attackers from stopping.
Get the latest news, expertise, exclusive resources, and industry leaders for free.